ADT-1 Android TV
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong." This page will be dedicated to a general overview of descriptions and information related to the ADT-1 Android TV.
Purchase
The ADT-1 is not available for purchase and is only obtained through purchase from individuals who obtained a unit at Google IO or through the official "Request an ADT-1" page.
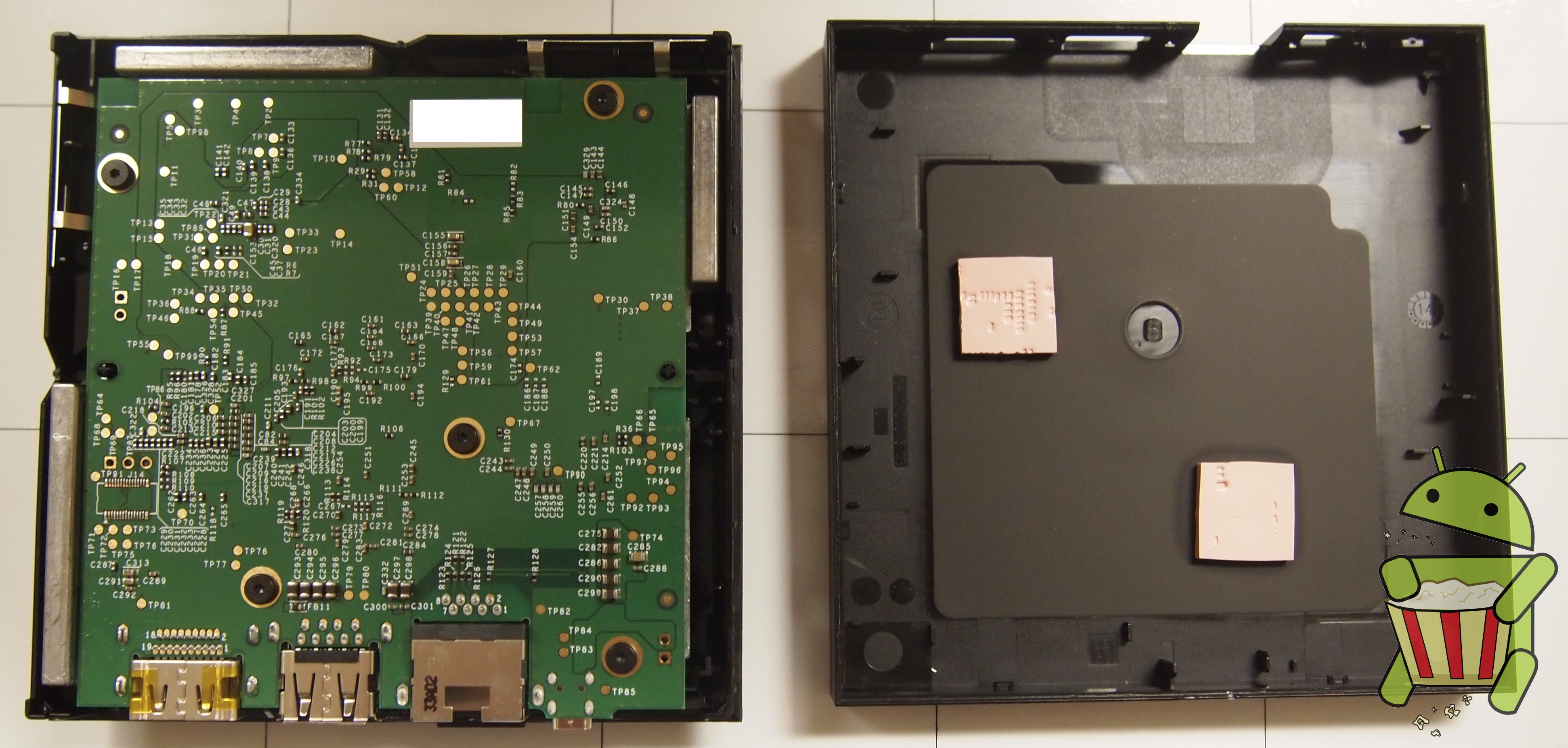
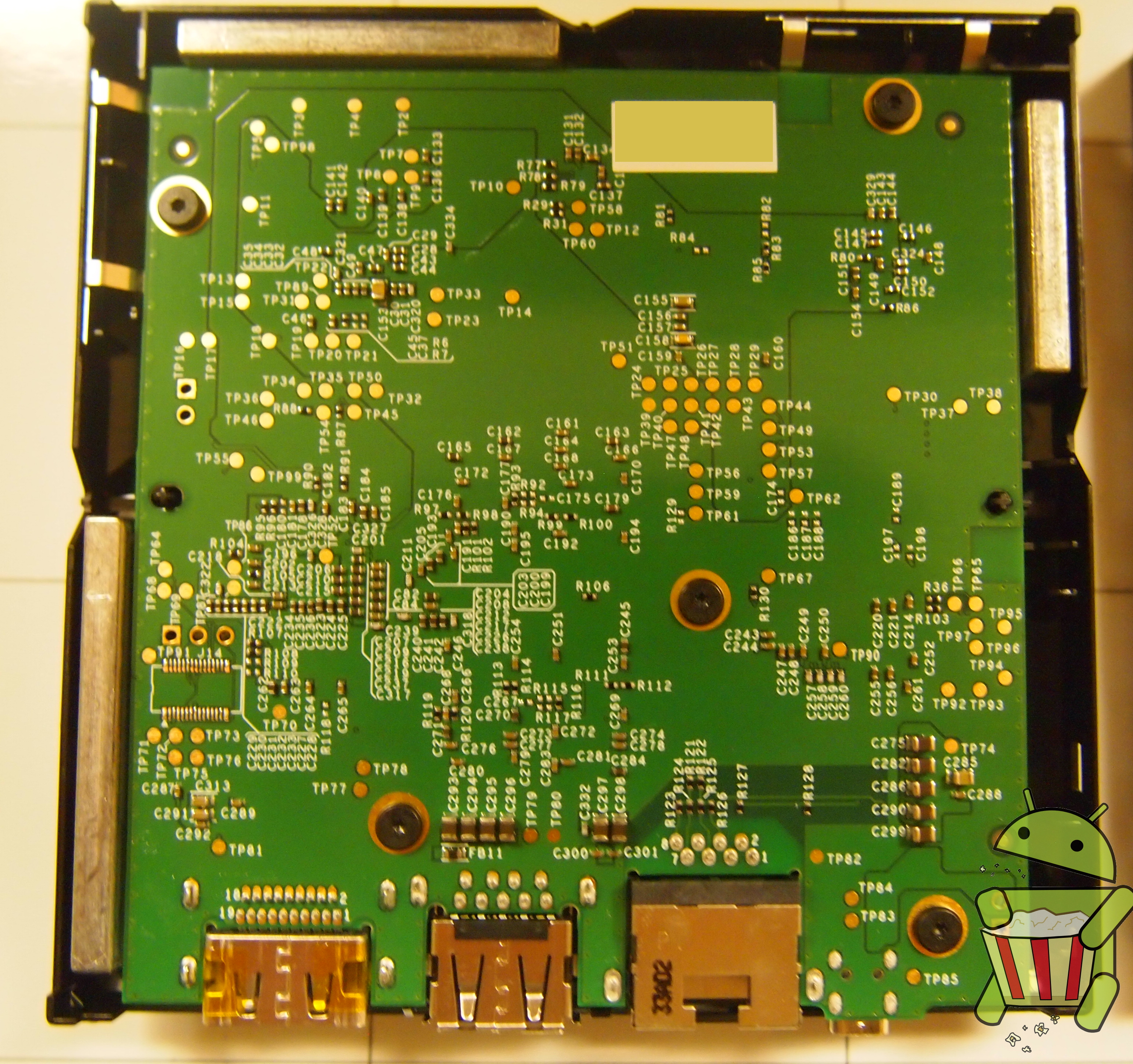
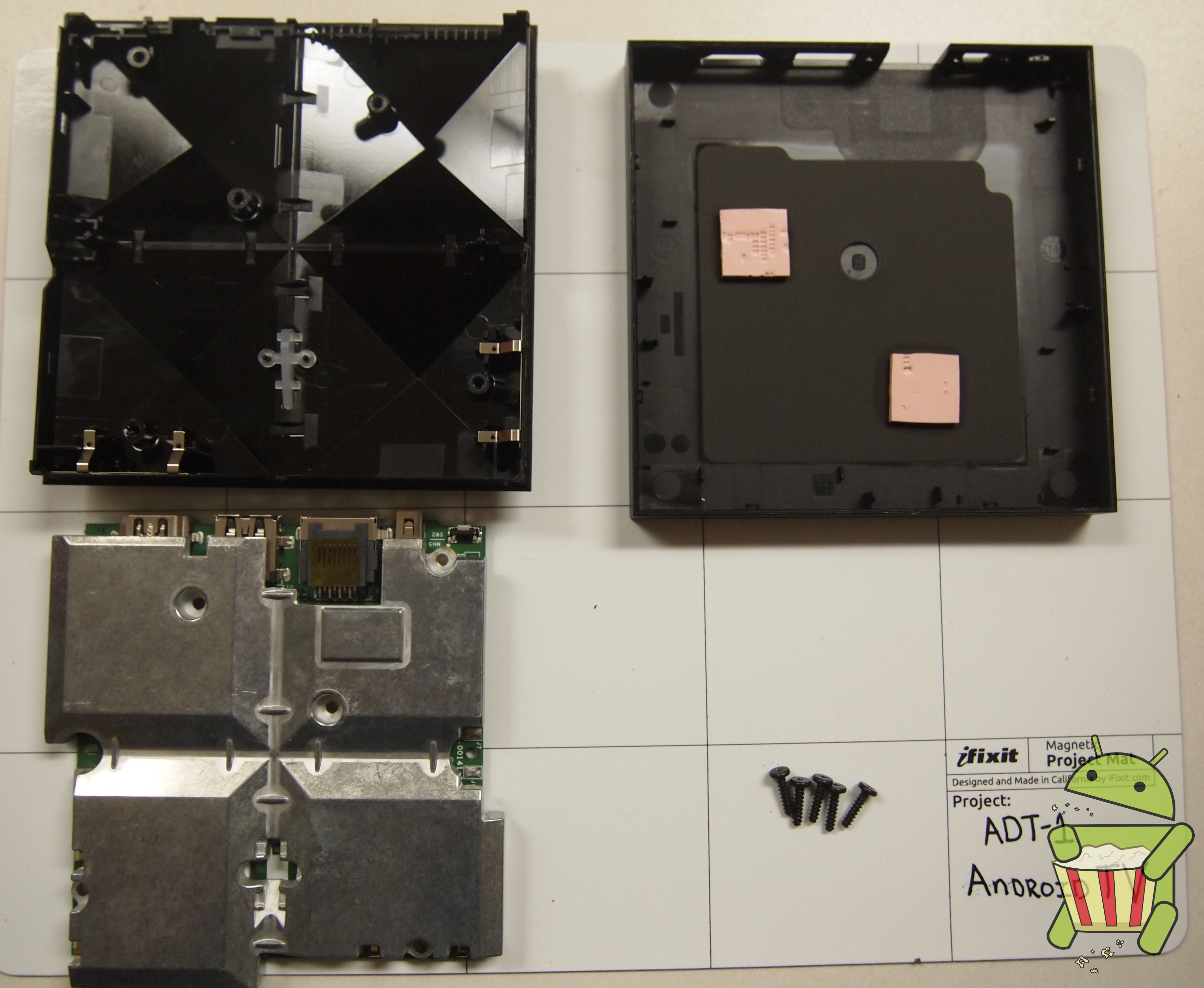
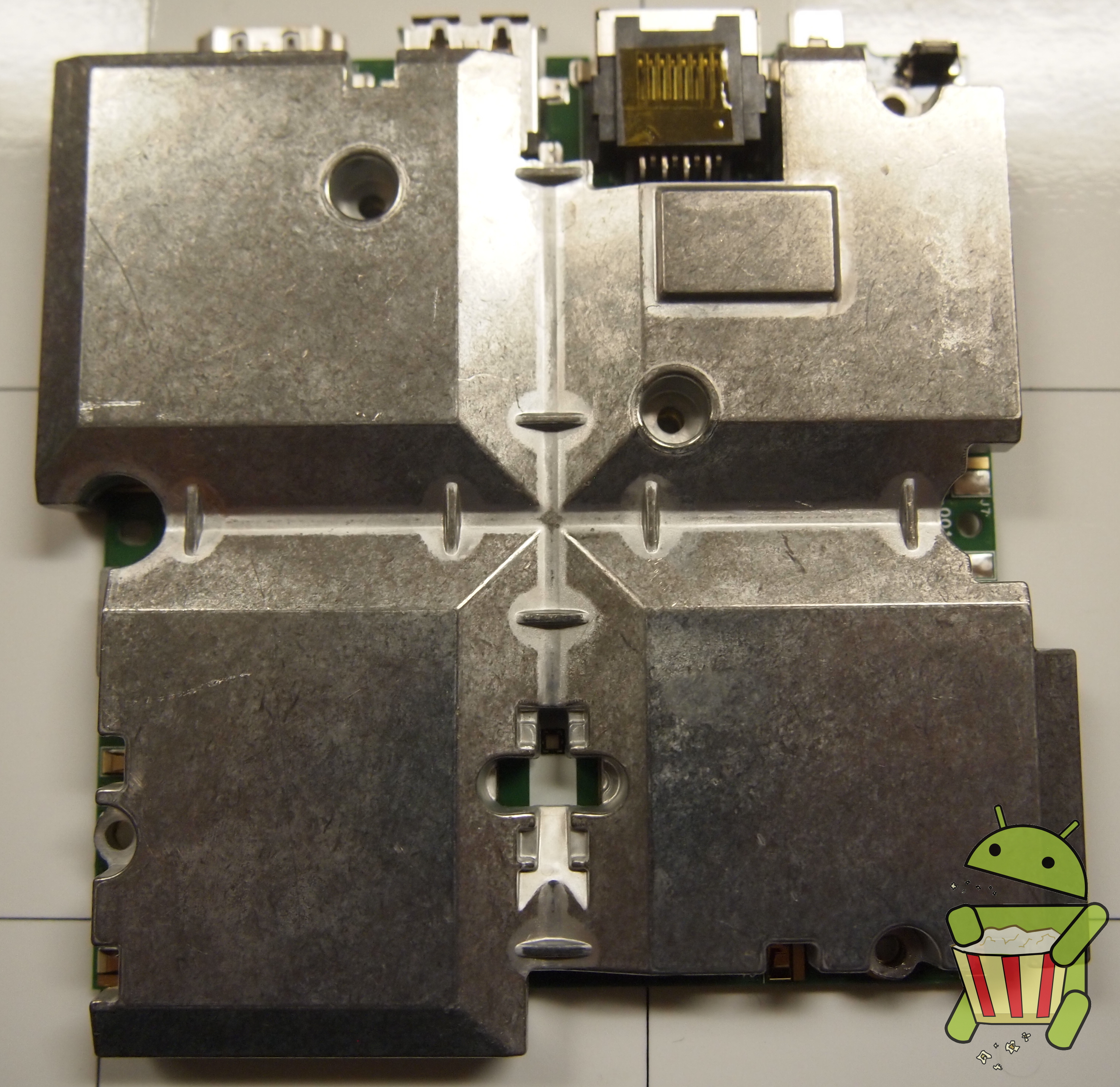
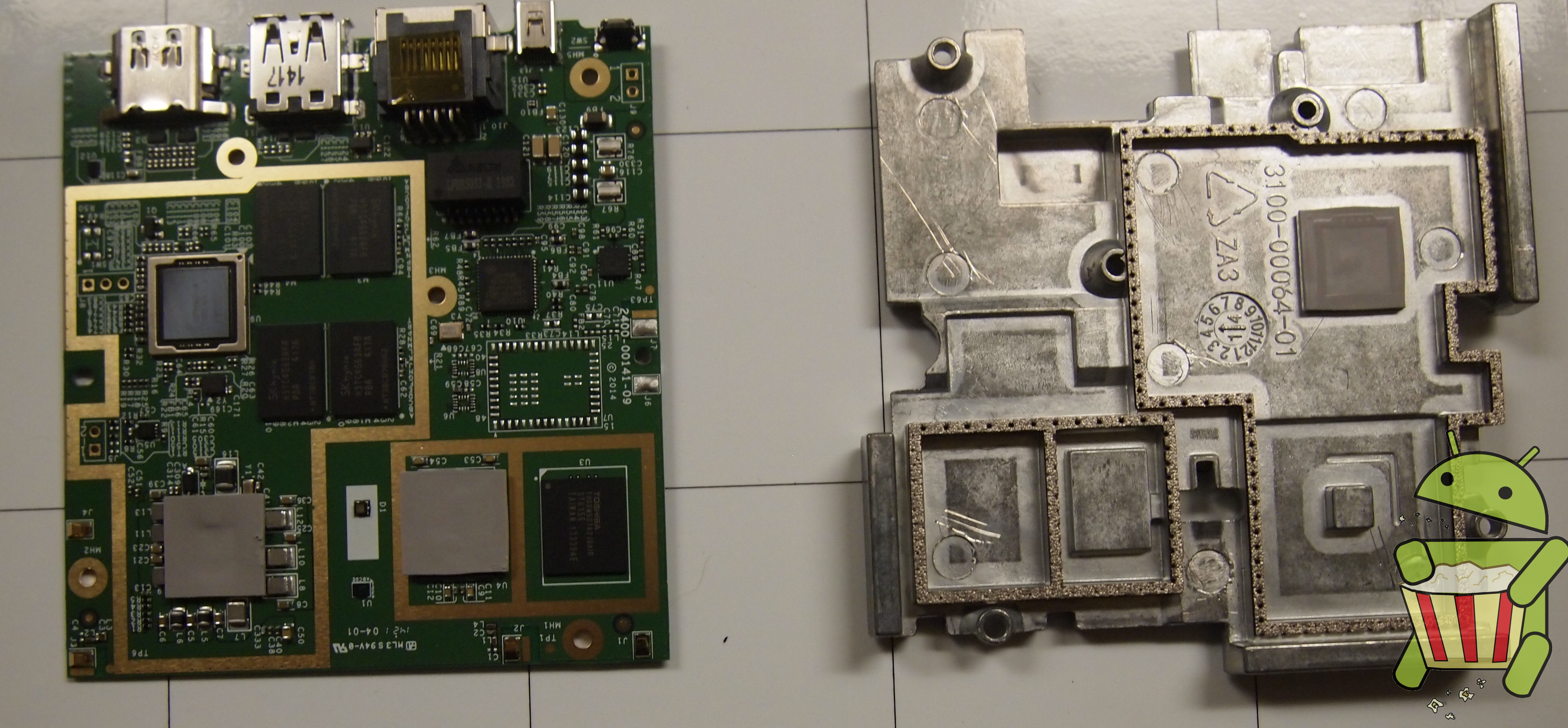
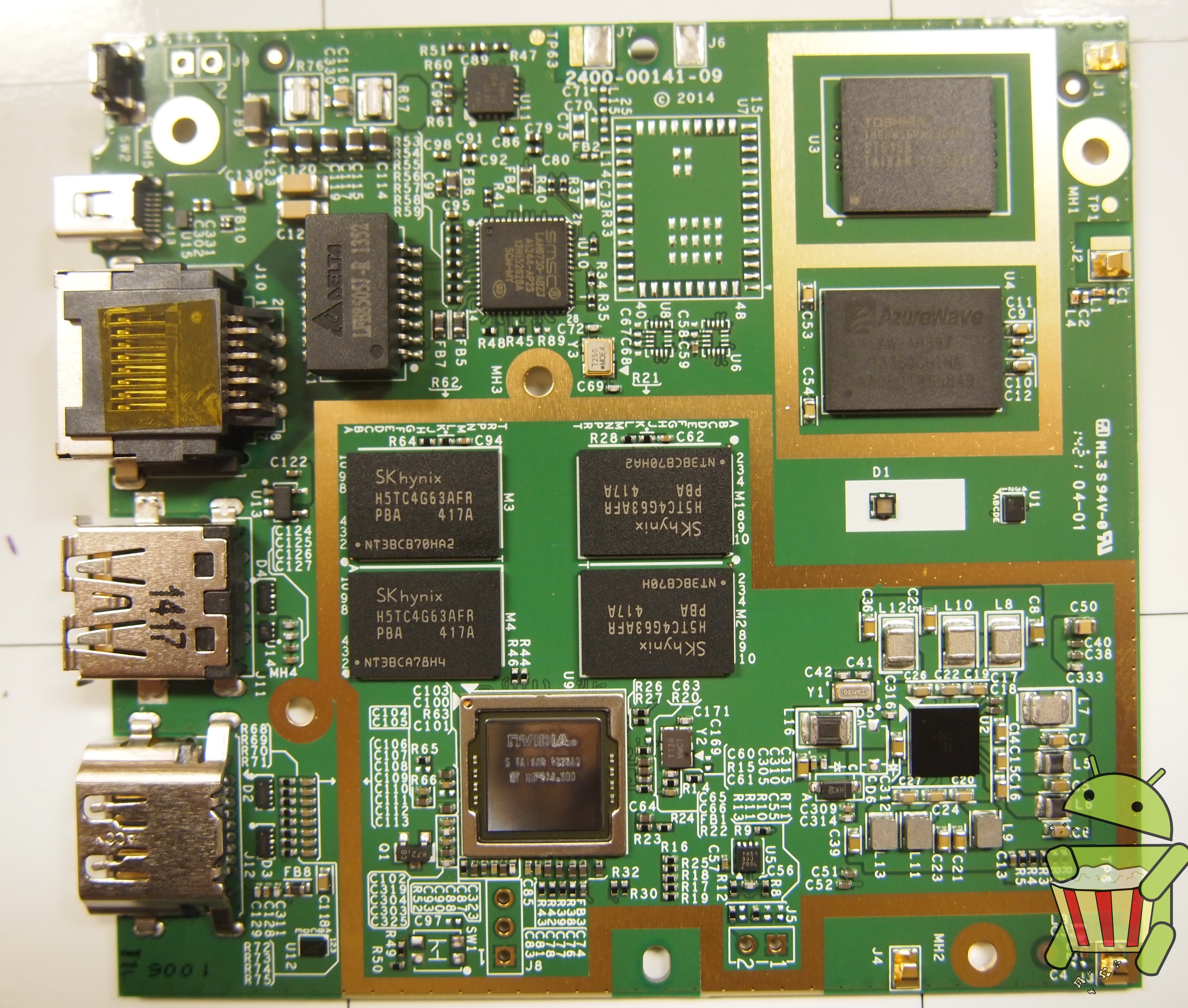
Tear Down
The ADT-1 Android TV is pretty easy to get apart once all the clips holding the case together are undone. In this tear down we used a razor blade but a guitar pick or similar small and durable piece of plastic is recommended.
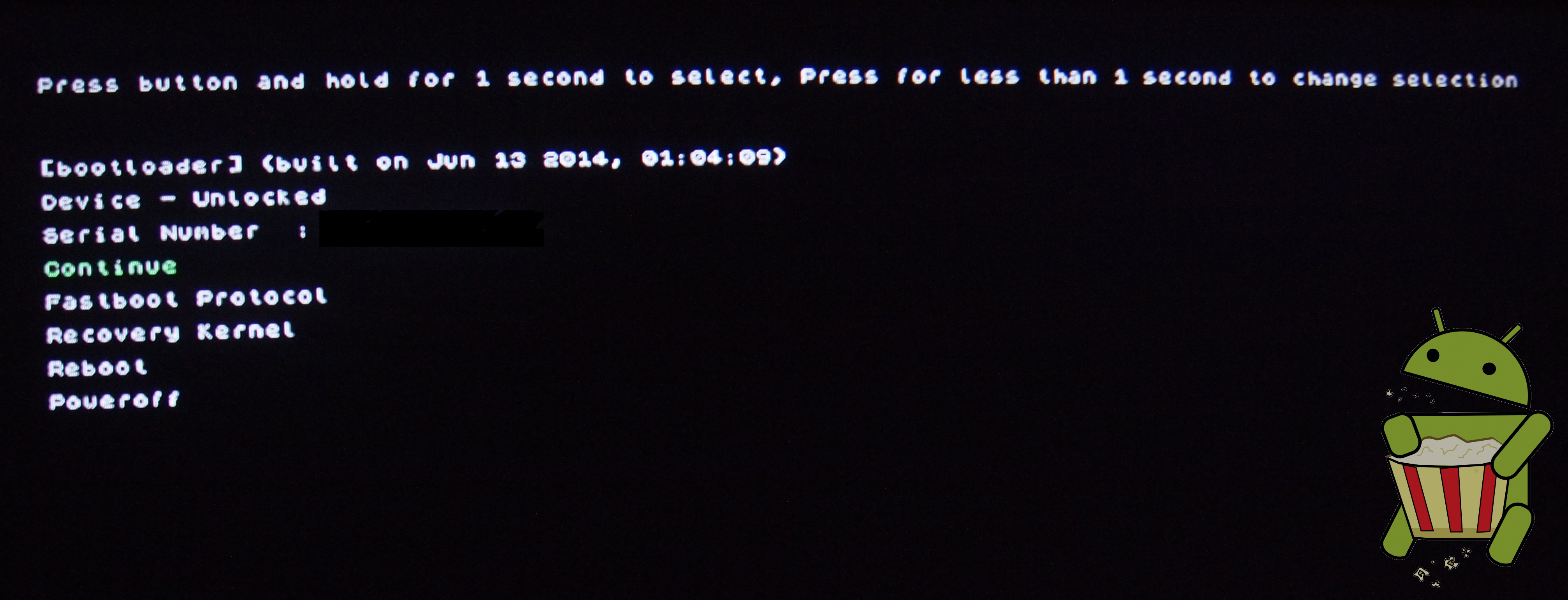
Accessing Fastboot
- The bootloader on the ADT-1 distributed from Google IO comes unlocked. Below is the process on accessing fastboot interface.
Steps to enter recovery mode
- Hold reset button on back of ADT-1 for approximately 10 seconds or until device reboots.
- Screen will display fastboot options as seen in picture to the left. A short click of the reset button navigates while a long click selects.
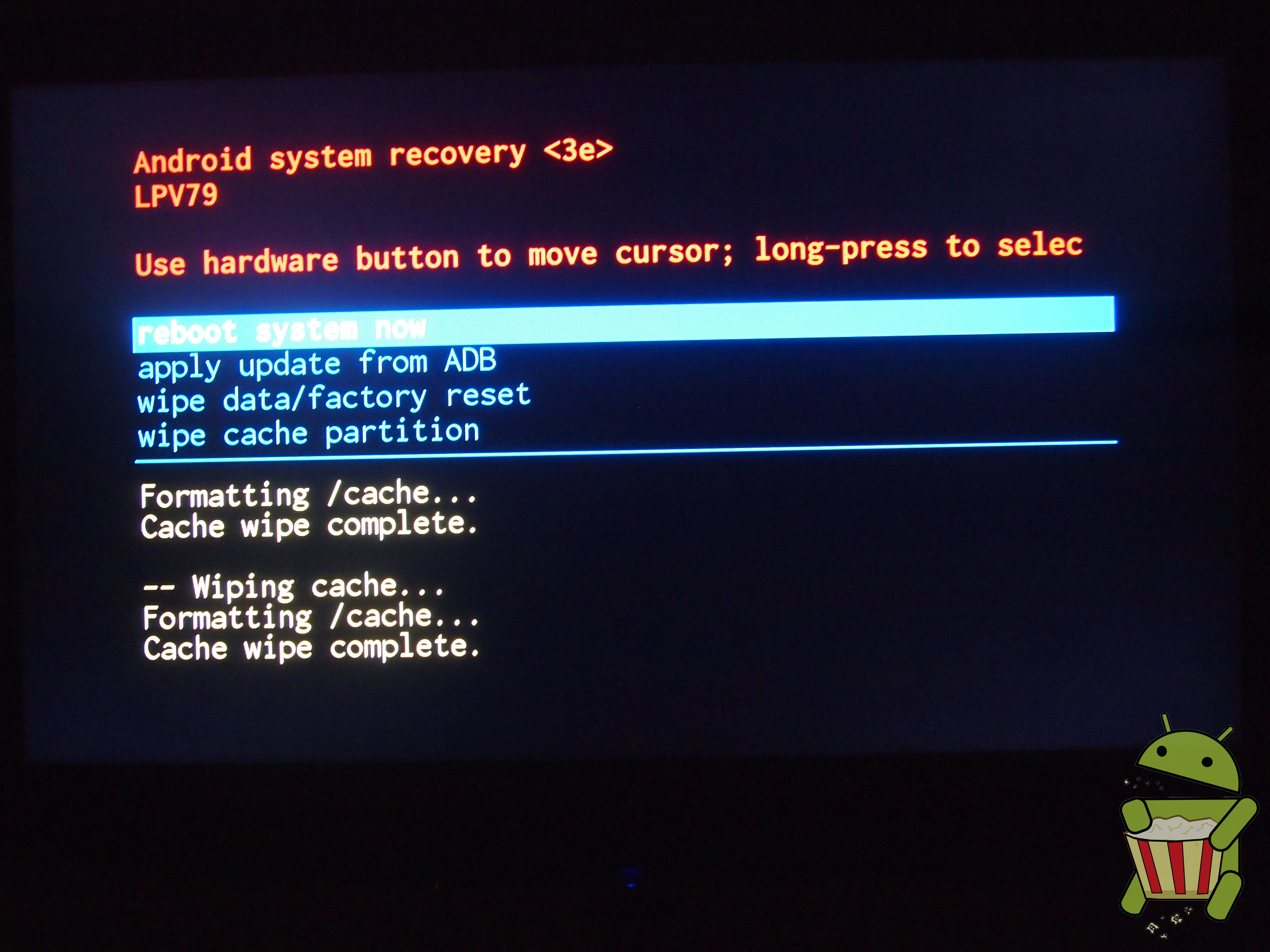
Accessing Recovery
On the ADT-1 the standard "Android Recovery (3e)" is used. The menu for this mode is hidden behind Auto-Recovery functionality which clears the user-data and cache partitions.
Steps to enter recovery mode
- Through adb using "adb reboot recovery"
- Through the fastboot menu accessed with the process above.
- By holding the reset button for roughly 20 seconds.
Bootloader Vars
- A list of the bootloader variables obtained from using fastboot and issuing "fastboot getvar all" can be found at ADT-1 Fastboot Bootloader Variables
Build.prop
- A sample build.prop from an Android TV ADT-1 device can be found at ADT-1 Android TV Sample Build.prop
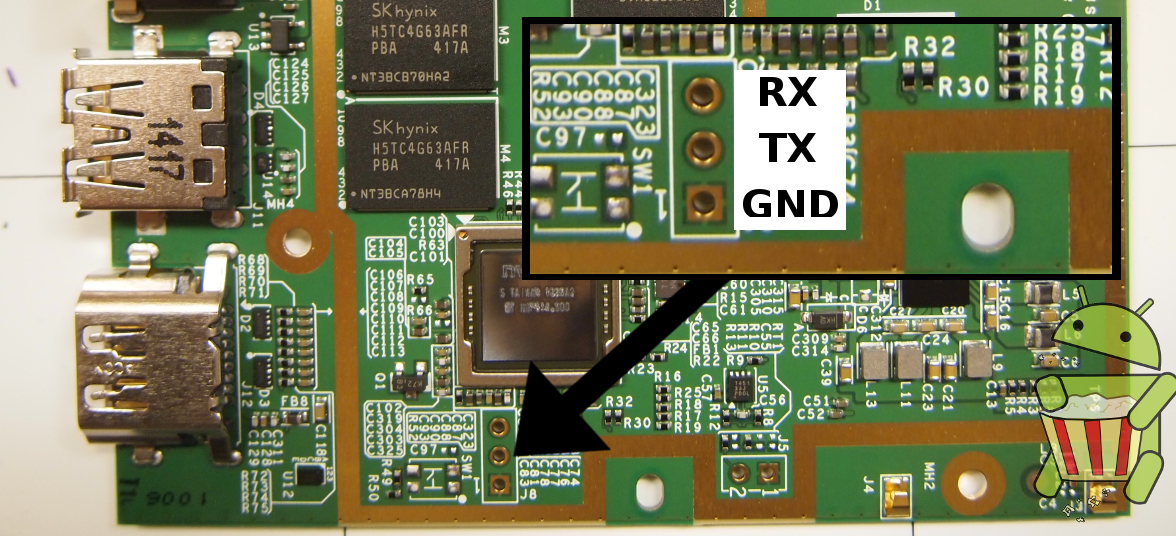
UART Pinout
- UART console output as well as access to the FIQ Debugger is available by connecting a UART adapter to the ADT-1.
SysRq
- SysRq is available with the following commands.
SysRq : HELP : loglevel(0-9) reBoot Crash terminate-all-tasks(E) memory-full-oom-kill(F) kill-all-tasks(I) thaw-filesystems(J) show-backtrace-all-active-cpus(L) show-memory-usage(M) nice-all-RT-tasks(N) powerOff show-registers(P) show-all-timers(Q) Sync show-task-states(T) Unmount show-blocked-tasks(W) dump-ftrace-buffer(Z)
FIQ Debugger
- FIQ Debugger is available with the following commands.
debug> help FIQ Debugger commands: pc PC status regs Register dump allregs Extended Register dump bt Stack trace reboot [<c>] Reboot with command <c> reset [<c>] Hard reset with command <c> irqs Interupt status sleep Allow sleep while in FIQ nosleep Disable sleep while in FIQ console Switch terminal to console cpu Current CPU cpu <number> Switch to CPU<number> ps Process list sysrq sysrq options sysrq <param> Execute sysrq with <param>
boot.img
(@GiantPune) on our IRC channel #GTVHacker rooted his ADT-1 using the Android Futex kernel exploit and dumped his boot.img. You can use this with fast-boot to root your ADT-1.
Updates
Along with the initial OTA another file was transmitted just prior to the OTA update.
- models-v2.zip Thanks _halfluck_.
- Initial OTA: molly-LPV79-from-KMV35 Thanks _halfluck_.
- Second OTA: molly-LPV79 Thanks luxferro397